Memcached Monitor Configuration Guide on the Elven Platform
The Memcached Monitor from the Elven Platform enables checks based on key queries in Memcached. This feature helps configure continuous checks, set alerts, and define thresholds for automatic incident creation, ensuring you are quickly informed of any irregularities in connectivity or service performance.
Memcached is an open-source caching system designed to improve application performance by storing frequently accessed data in memory. It uses a simple key-value model to temporarily store data, enabling fast responses and reducing the load on databases or underlying services. Widely adopted in web applications, e-commerce platforms, and systems that require high performance, Memcached stands out for its horizontal scalability, support for multiple servers, and easy integration with various programming languages.
With features like in-memory storage, efficient data distribution, and simple management, Memcached is a reliable solution for accelerating response times and optimizing resource usage in modern applications.
Accessing Memcached Monitoring:
Navigate to the main menu and click on Services Hub.
In Cache, select the Memcached item.
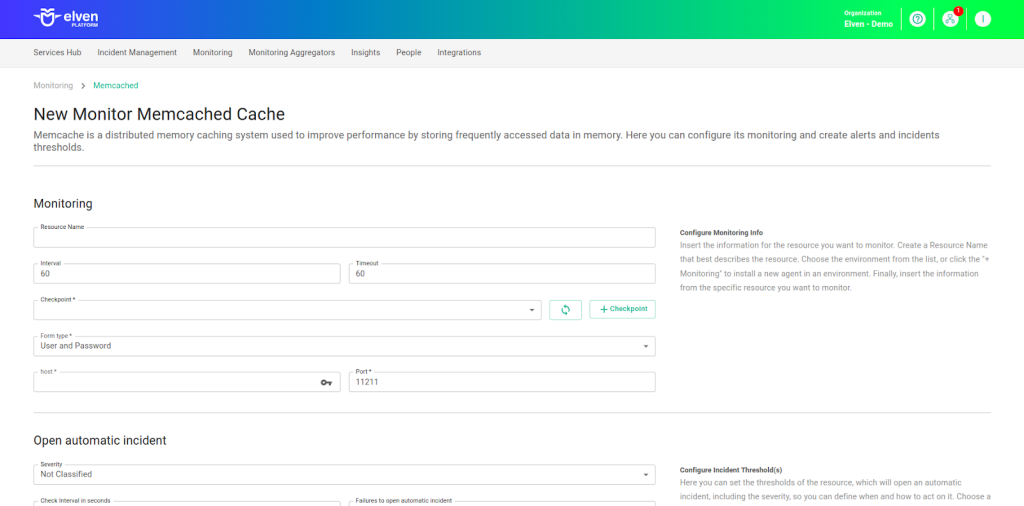
Monitoring Configuration
Monitoring the availability of your services has never been easier. Start by giving a clear name to the resource you want to monitor (Resource Name) to make identification easier. Then, adjust the Interval between checks and the Timeout for receiving a response.
Select where the monitoring agent is located (Checkpoint Cloud) by choosing the appropriate Environment. If it doesn’t exist, you can create one using + Checkpoint. After this setup, in Form Type, you can choose between User and Password or Healthcheck URL.
In User and Password, enter the Host (server address) and the Port, which by default is 11211, but can be adjusted if the service is configured on a different port. In Healthcheck URL, simply enter the URL of the resource to be monitored.
Keep in mind that the Host and Healthcheck URL fields only accept URLs. If you need to use an IP address, it must be stored in a Secret to ensure security and organization of sensitive information.
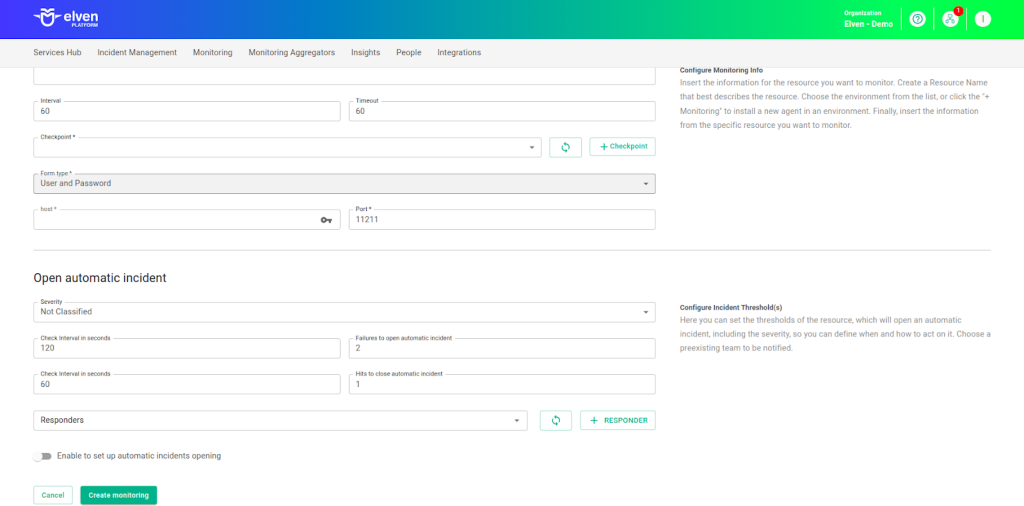
Automatic Incident Opening
You can configure automatic incident opening to ensure a quick response to critical issues. To begin, define the incident severity, allowing you to prioritize according to urgency. Next, adjust the Check Interval, specifying the check frequency in seconds to continuously monitor the resource. This helps ensure you're always one step ahead, detecting problems as soon as they arise.
Additionally, select the team to be notified whenever an incident occurs and enable the "Enable to set up automatic incidents opening" option to ensure the configuration is active. With this setup, the platform automates incident management, making the response process faster and more efficient, without the need for manual intervention. This ensures your team is always ready to resolve any issue with speed and precision.
Maintenance Window
We still have the Maintenance Window, which is an essential feature for managing planned maintenance periods in your application. During this interval, checks are temporarily paused, preventing monitoring, alerts, and notifications from being triggered while you perform adjustments or updates. This allows maintenance to proceed smoothly, without generating unnecessary notifications or false alarms, ensuring that your operation continues in an orderly manner without unexpected interruptions in performance reports.
For example, imagine you need to update the payment system of an e-commerce platform by making backend adjustments, such as installing new security certificates. To do this, you can configure the Maintenance Window for a specific time, such as 12/13/2024, from 2:00 PM to 2:30 PM. During this period, the Elven Platform suspends checks, preventing the monitoring system from recording temporary failures or triggering false alerts. This way, you can make the necessary changes calmly, knowing that the monitoring system will not be impacted during maintenance. This approach ensures that the update is carried out in an organized manner, without affecting the user experience or generating unwanted notifications.
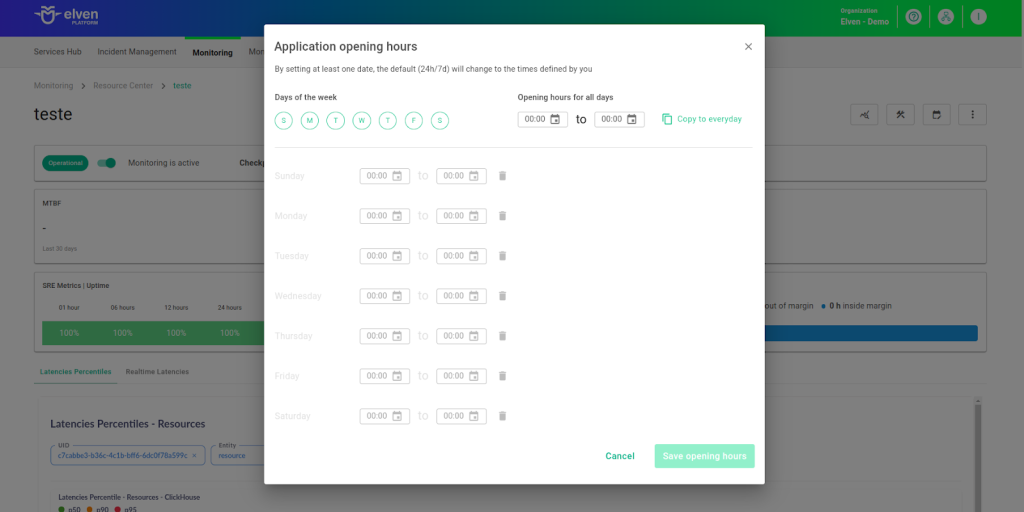
Application Opening Hours
You can also rely on the Application Opening Hours feature, which allows you to configure your application's operating hours. This functionality is essential for customizing monitoring based on the periods when your application is actually active, avoiding alerts and notifications outside of business hours. This way, monitoring becomes more aligned with your business's real needs, ensuring more accurate reports and efficient management.
For example, imagine your application only operates from Monday to Friday, from 9:00 AM to 6:00 PM. You can configure Application Opening Hours to reflect this schedule by specifying the working days and time periods. With this setup, the Elven Platform automatically disables checks outside of these hours, preventing the logging of failures that do not affect end users and avoiding unnecessary alerts. This approach optimizes performance analysis, focusing only on relevant periods and providing a clearer view of your application's health during its operating hours.
Glossary of Technical Terms
Memcached: An open-source caching system widely used to boost application performance by storing frequently accessed data in memory. It uses a simple key-value model for temporary caching, reducing the load on databases and improving responsiveness. Known for its high performance, horizontal scalability, and support for multiple servers, Memcached is ideal for web applications, e-commerce platforms, social networks, and systems that require low latency. Its simplicity and integration with various programming languages make it an efficient solution for optimizing response time and resource usage in modern applications.
Interval: The time interval between automatic checks performed during monitoring.
Timeout: The time limit for the monitoring system to receive a response from the monitored resource before registering a failure.
Checkpoint Cloud: The location where the monitoring agent is hosted, which can be a pre-existing environment or one created by the user.
Host: The address (URL) of the monitored resource. If an IP address is required, it should be stored in a Secret for enhanced security.
Secret: A resource used to store sensitive information, such as IP addresses or credentials, ensuring security and organization.
Enable to set up automatic incidents opening: An option that, when enabled, allows the automatic creation of incidents upon detection of critical issues.
Severity: The level of criticality assigned to an incident, allowing it to be prioritized according to its urgency.
Check Interval: The time interval, in seconds, for performing continuous checks on the monitored resource.
Maintenance Window: A feature that temporarily pauses monitoring, alerts, and notifications during planned maintenance periods.
Application Opening Hours: A configuration that defines the operating hours of the application, aligning monitoring with active periods and avoiding alerts outside those hours.
Last updated
Was this helpful?

